
Thursday, May 15, 2025
Quantum Computing's Threat to Bitcoin: Understanding the Risk and Potential Solutions
The emergence of quantum computing represents one of the most significant technological challenges to Bitcoin's security model. While classical computers would take billions of years to break Bitcoin's cryptographic foundations, quantum computers could potentially accomplish this feat in hours or even minutes. This represents an existential risk that the Bitcoin community must understand and prepare for proactively.
Understanding the Quantum Threat Vector
Bitcoin's security relies primarily on the Elliptic Curve Digital Signature Algorithm (ECDSA), which creates mathematically linked public and private key pairs. The security assumption behind ECDSA is that deriving a private key from a public key is computationally infeasible using classical computers—a problem known as the elliptic curve discrete logarithm problem (ECDLP).
However, in 1994, mathematician Peter Shor developed Shor's algorithm, which demonstrated that quantum computers could solve this exact problem exponentially faster than classical computers. A sufficiently powerful quantum computer running Shor's algorithm could break Bitcoin's ECDSA cryptography, potentially allowing attackers to steal funds from any address where the public key is exposed.
According to research from the University of Sussex, a quantum computer with approximately 1.9 billion qubits could breaking Bitcoin's 256-bit encryption in 10 minutes. While current quantum computers are far from this capability (IBM's largest quantum processor has 127 qubits), the technology is advancing rapidly.
Bitcoin's Specific Vulnerabilities
Bitcoin's vulnerability to quantum attacks varies based on how addresses are structured and used:
1. Pay-to-Public-Key (P2PK)
The earliest Bitcoin addresses directly exposed public keys on the blockchain. Research by River indicates these addresses hold approximately 2 million BTC across 45,800 UTXOs, representing billions of dollars at risk.
2. Pay-to-Public-Key-Hash (P2PKH)
These addresses (starting with "1") hash the public key, providing one layer of quantum resistance. However, the public key becomes exposed when spending from these addresses. According to Deloitte's quantum security assessment, approximately 4 million additional BTC sits in reused P2PKH addresses where public keys were previously revealed.
3. Address Reuse
Any address that has been used to send funds (not just receive) has exposed its public key on the blockchain, making it vulnerable to quantum attacks. This practice is unfortunately common among Bitcoin users despite security recommendations against it.
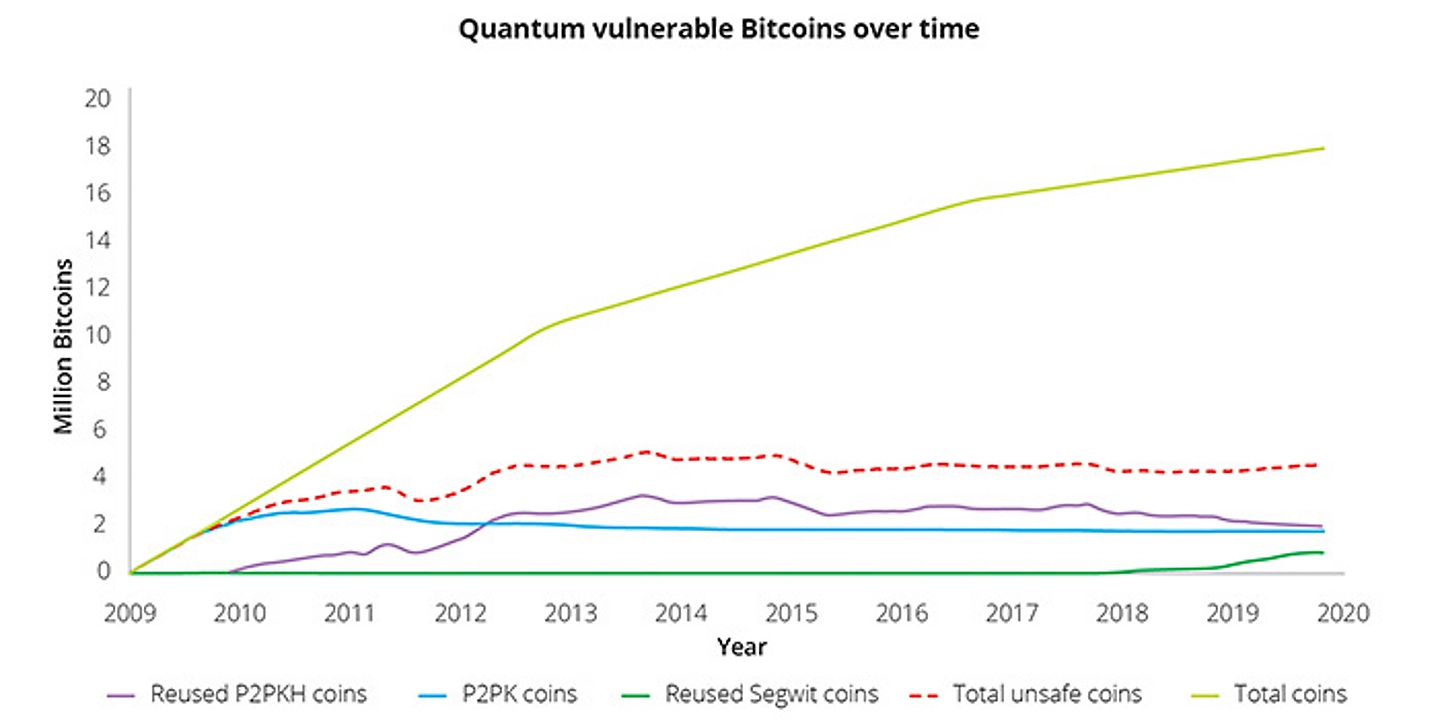
Bitcoin Addresses at Risk from Quantum Computing. Source: Deloitte
Attack Scenarios: The Timeline Problem
Quantum threats to Bitcoin can be categorized as:
Short-range Attacks
When you broadcast a transaction, there's approximately a 10-minute window before confirmation. A quantum attacker could potentially:
- Observe your transaction in the mempool
- Extract your public key
- Use Shor's algorithm to derive your private key
- Create a competing transaction sending your funds to themselves
- Attach a higher fee to ensure their transaction confirms first
According to research from the University of London, this attack would require quantum computers capable of executing Shor's algorithm in minutes—a capability that could emerge within the next decade.
Long-range Attacks
This more dangerous scenario involves attacking addresses with previously exposed public keys. Since these keys are permanently recorded on the blockchain, attackers have unlimited time to break the cryptography. Based on the numbers mentioned previously, once quantum computers reach sufficient power, approximately 25% of all Bitcoin could be vulnerable.
Quantum-Resistant Solutions
Post-Quantum Cryptographic Algorithms
The National Institute of Standards and Technology (NIST) has been evaluating quantum-resistant cryptographic algorithms. Their standardization process has identified several promising candidates:
- CRYSTALS-Dilithium: A lattice-based signature scheme offering a good balance between key size and security.
- FALCON: Another lattice-based approach with smaller signatures but more complex implementation.
- SPHINCS+: A stateless hash-based signature scheme that relies only on hash functions, which are believed to be quantum-resistant.
These algorithms could replace ECDSA in Bitcoin, though they would significantly increase transaction sizes and verification times.
Soft Fork vs. Hard Fork Approaches
Soft Fork Solutions
On example its Bitcoin proposal BIP-360 suggest implementing post-quantum signatures through a soft fork. This would:
- Create new address types that use quantum-resistant algorithms
- Allow a gradual transition without forcing all users to upgrade
- Enable a hybrid approach combining classical and quantum-resistant signatures
The advantage is backward compatibility—old nodes would still recognize new transactions as valid, even if they can't fully validate the quantum-resistant components.
Hard Fork Considerations
Some researchers argue that a hard fork might eventually be necessary. One draft Bitcoin improvement Proposal is Quantum-Resistant Address Migration Protocol (QRAMP) by Agustin Cruz. This will:
- Enforce to fully migrate Bitcoin to quantum-resistant cryptography
- Set a deadline for the miration after which older versions of the blockchain will be incompatible
- Potentially invalidate or sweep "at-risk" UTXOs that haven't migrated to quantum-resistant addresses
While controversial, some suggests a carefully managed hard fork could accelerate Bitcoin's quantum security transition.
Taproot's Role in Quantum Resistance
Taproot, activated in November 2021, provides a pathway toward quantum resistance through its enhanced scripting capabilities. Taproot enables:
- More complex spending conditions through MAST (Merkelized Abstract Syntax Trees)
- The potential implementation of quantum-resistant signature schemes within script paths
- A transitional security model where funds could require both ECDSA and quantum-resistant signatures
Wallet Security Strategies: What You Can Do Now
Despite the future threat, several strategies can reduce quantum risk today:
1. Avoid Address Reuse
The simplest protection is creating new addresses for every transaction. This is a good practice that prevents public key exposure until you spend from an address.
2. Leverage Modern Address Types
Newer address formats like Pay-to-Witness-Public-Key-Hash (P2WPKH, starting with "bc1") and Pay-to-Taproot (P2TR, also "bc1" but different format) don't provide quantum resistance themselves but integrate with Bitcoin's upgrade path toward quantum-resistant solutions.
3. Consider HD Wallet Derivation Paths
Hierarchical Deterministic (HD) wallets using BIP-32 create chains of keys from a single seed. While sharing an Extended Public Key (xpub) creates potential vulnerability, using hardened derivation prevents quantum computers from deriving child private keys even if they compromise the parent public key.
The xpub key derivation depends on hash functions rather than ECDSA, providing some quantum resistance for your wallet hierarchy even if individual addresses remain vulnerable.
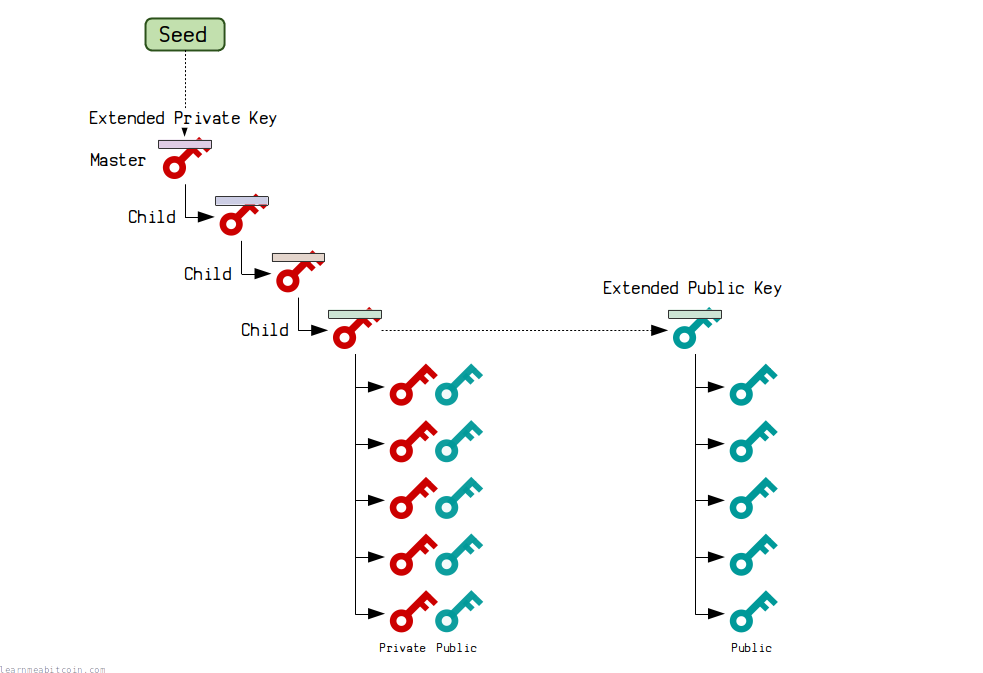
Hierarchical Deterministic wallet structure showing hardened derivation paths. Source: Learn me Bitcoin
The Transition Timeline
Current estimations suggest that Bitcoin has approximately 5-10 years before quantum computers might threaten its cryptographic security. This timeline depends on:
- The pace of quantum hardware development
- Advances in quantum error correction
- The Bitcoin community's response in implementing quantum-resistant solutions
Microsoft's recent announcement of their Majorana chip represents a potential acceleration in quantum computing progress, potentially shortening this timeline.
Conclusion: Balancing Concern with Preparation
The quantum threat to Bitcoin is real but manageable with proper preparation. While catastrophic scenarios make headlines, the reality is that:
- The Bitcoin community has already demonstrated the ability to implement protocol upgrades
- Quantum computing advances are observable, providing warning signs before critical thresholds
- Post-quantum cryptography solutions exist and are being refined
The greatest risk isn't the technology itself but complacency in addressing the threat. By understanding which addresses are vulnerable, supporting development of quantum-resistant Bitcoin proposals, and adopting good security practices today, the Bitcoin ecosystem can navigate this challenge while preserving its core security guarantees.
As developers and users in the Web3 space, our responsibility is to build with this transition in mind, ensuring that long-term Bitcoin holdings remain secure regardless of quantum computing advances. The journey toward quantum resistance represents not just a technical challenge but an opportunity to strengthen Bitcoin's foundational security for decades to come.
How Can We Help?
Implementing a robust HD wallet for Bitcoin is effortless with Jetnodes’ Blockbook API. Our xPub support lets you:
- Fetch UTXOs for every child address under your extended public key, so you always know exactly which outputs are available to spend.
- Aggregate real-time balances across the entire HD wallet in a single request, eliminating the need to poll each address individually.
- Fetch complete transaction histories—including confirmations, timestamps, and metadata—for all derived addresses with one unified endpoint.
Whether you’re building a light wallet, a custodial solution, or an analytics dashboard, Jetnodes handles the indexing and caching so you can focus on delivering the best user experience.
Ready to get started?
- Create your free Jetnodes account now for full Blockbook access—no credit card required.
- Explore all xPub and address-based methods in our documentation
Unlock seamless HD wallet support today with Jetnodes.